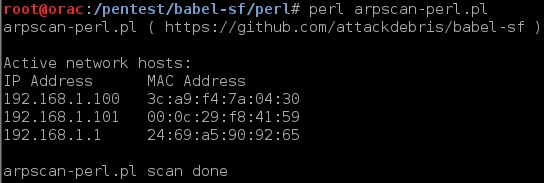
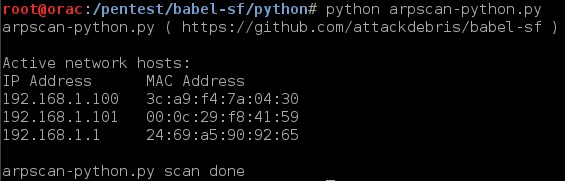
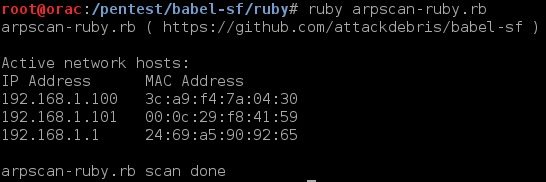
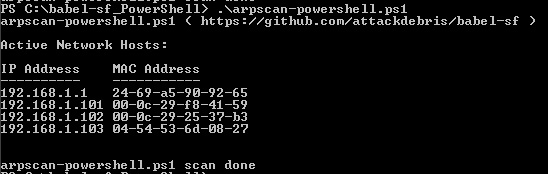
The fifth BruCON conference was held 26th to 27th of September 2013 in Ghent, Belgium. From the off, the conference had a great feel, its organised by a group of security enthusiasts as a non-profit organisation and they do a great job. From the live classical piano playing in the lounge/rest area where you have you meals; breakfast, lunch and dinner (which are all included in the low price) to the large screen displaying all the recent #BruCON twitter activity it makes for an enjoyable couple of days. The conference was organised into a single (main auditorium) speaker track and 2 hands-on lab tracks in the afternoon. Whilst you’re wholly free to mix and match between the main track and the lab tracks, I focused on the main speaker track (although I did hear that the labs were also excellent!), my vague recollections and highlights can be found below.
HTTP Time bandit – Vaagn Toukharian
The tool is basically a tool to perform resource usage denial of service (DOS) type attacks against layer 7 or as referred to during the talk “HTTP GET flooding with spice”. In essence the tool performs a GET flood but some analysis is done before flooding takes place.
The tool first conducts a spider of the site to determine and collect the transfer times for each resource, the average speed of transfers are calculated. Once complete the resource(s) That have the slowest average transfer time(s) are calculated; effectively CPU intensive resources take longer to respond and this is what we are identifying here. To remove false positives from the returned data set statistics are used to analyse the data and discard resources that have a large degree of variance i.e. non consistent time delays that have another cause e.g. network latency.
The tool is available on the GitHub link: https://github.com/Qualys/timeBandit
The speakers moved on to discuss traditional DDOS defences in the form of load balancing and commercial protection services e.g. cloud based solutions, identifying and fixing resource hogs, apache configuration options and other apache modules advanced mod_security protection
The speakers suggested that Timebandit can be used itself to identify and fix these resource hogs. And went on to state that in an ideal world the tool itself would generate configuration files to protect the system (stating this was unlikely to happen).
The following Apache modification options were discussed:
- mod_security – offers simple protections that reduced an unprotected attack (i.e. without the change) with a CPU threshold of 98% down to a CPU load of 0% (with the change applied)
- mod_limitpconn – limits the number of downloads
- mod_qos – provides resource management options
- mod_bwshare – accepts or rejects connections based on previous transactions with a source IP address
- mod_evasive – DOS/DDOS protection measures
- mod_httpbl – Makes use of project honeypot to gather a list of violators for the blacklist (it was suggested this was good in theory but hadn’t been examined in detail)
Taking the BDSM out of PCI with Open Source – Erin Jacobs and Zack Fasel
As most people who deal with it are only too painfully aware PCI DSS represents the Payment Card Industries, Data Security Standard.
- PCI compliance comprises of levels 1-4.
- Companies attempt to outsource the problem
- Open Source Solutions can be used for everything except external vulnerability scans.
- No clear PCI configuration guidelines, very generalised
The speakers have started the “Open PCI project.com”. With the aim to provide open source guidelines which are scalable, contain specific walk throughs and simple deployments via ready-to-go installations / virtual machines.
Although there are 12 PCI issues, the talk was only concerned about those that people are getting wrong, these issues in priority were:
- Logging: either not doing it well or spending too much money on it. Splunk whilst an excellent resource is too expensive. How about an open source option?
Linux = traditional options have been: syslog or deploying an agent.
Windows = Deploying an agent (most likely option) or integration with HIDS.
- Log server storage options were discussed “fluentd” was posed as a possible open source option to Splunk.
- File Integrity Monitoring: several options were discussed with the best suggested being OSSEC.
- Patch Management: it was stated that this probably the hardest thing to address with open source, but chef / puppet were suggested by a member of the audience as possible options.
- 2 factor authentication: OAUTH a hardware and software solution.
- AV – anomaly or ClamAV based or potentially binary white-listing.
CobraDroid – Jake Valletta
CobraDroid is a full-featured Android sandbox that includes the ability to modify device and radio identifiers, proxy network traffic with SSL validation bypassing, and perform per application method hooking, alerting, and packet capturing (and more!).
AppUse was discussed a closed source dynamic analysis tool.
CobraDroid setup:
Setup Android SDK, Download archives from his site, create new AVD (may have missed a stage here, see slides for full details).
CobraDroid runs Android 2.3, provides both Bash and Busybox which offers a much more user friendly testing environment.
CobraDroid Functionality:
The tools SSL validation bypass allows you to man in the middle SSL connections!
Application specific packet capture, uses custom iptables rules, resultant pcap files can be viewed wire shark.
Uses method hooking to alert on method calls – configured via the file /etc/hooks.conf
Project website: http://thecobraden.com/projects/cobradroid/
Real Time Analysis and Visualisation of Internet Status – Tiago Balgan Henriques, Tiago Martins, Joao Gouveia
Events are processed and analysed, as they happen, without storing large data volumes, enabling live actionable intelligence and rapid response capabilities for threat analysts and decision makers who want to stay ahead of emerging threats and opportunities or in other words “events, lots and lots of events”.
The huge amount and variety of data to tackle is difficult, a common API?
The speaker team have created a high performance scalable Complex Event Processor (CEP), uses streaming technology, follows publisher/subscriber model. Events are all handled in JSON format.
“StreamForce” = CEP
Search forms are entered and used to query the API
Real time feed services from multiple sources i.e. Honeypots, DNS, mail protection products.
Once the form is submitted It is possible to display a geographic maps showing botnet activity, Zeus activity etc. For example it would be possible to show the biggest botnets in any specific country.
Lightening Talks – Day 1
OWASP JAWS – Purpose: The purpose of the project is to have a workset with runnable java code that shows secure coding practices in a working way. Too many times developers end up at some developer forum where someone asks a question and the solutions (that may be working but not necessarily in a secure way) are copied and end up in production code:
https://www.owasp.org/index.php/OWASP_JAWS_Project
DNS Amplification Attacks – Lucas Kauffman some very good slides that should be read in their entirety:
http://www.slideshare.net/lucaskauffman/avoiding-dns-amplification-attacks
The curious case of 43.0.20.80 – Speaker was trying to determine why one host was always resolving Google.com to a non Google related IP address in China i.e. 43.0.20.80. It turned out that DNS responses were being resolved to IPV6 addresses but interpreted as IPV4 addresses by affected hosts i.e. decoded and always resolving to 43.0.20.80 i.e this address hosted in China.
HTTP2.0 (Speedy) – Google’s implementation accepted as the new standard – makes use of header compression both client and server side. Not pull and request as old implementations but multiple simultaneous conversations – Burp doesn’t work with it! It’s all SSL, Web over UDP as well as TCP.
Day 2
Paint by numbers vs Monet – Russ Gideon
Analysis of APT attacks has shown that an MSF module has been seen in APT attacks 7 of 22 in the CVE PDF exploit discussed, the only change from the default MSF module was that the shellcode changed and obfuscation was added but it was the same basic code in use on the whole.
Once access has been gained: long term back doors established, credential harvesting, lateral movement, mimikatz (can be their own version), PTH toolkit, their own psexec.exe. Dropper installs a service. Remote named pipes for all communications.
The speakers have created a custom psexec module (on GitHub), to hide from forensics, AV etc.
Discussed a black hat group: installed 3 x back doors on each host, used UPX for packing (i.e. old/lame) and self extracting RAR file, they attacked sticky keys (sethc) and magnify for privilege escalation. SYSTEM$ user added and the user was also added to the local admins group, password identified was “qazwsx!#123”
In conclusion they summarised that APT attacks were not highly sophisticated, the groups behind the attacks do not think like pentesters, they think forensically and opportunistically.
Conclusion: pentesters usually have a much different footprint and end goals than those of APT operators / Nation States.
Data Plane Networking – Robert Graham
Apache/Bind should not be exposed to the Internet they were designed for the Internet that existed in the late 90’s and are not robust/ruggedised enough for today’s Internet (I paraphrase here). The speaker suggested using an exokernel i.e every event has its own thread and a virtual network adapter. A more short term solution is to make use of Nginx (as opposed to Apache) and other DNS servers (as opposed to Bind) faster.
Building Custom Android Malware for Pen Testing – Stephan Chenette
Android uses the Dalvik Virtual Machine. Malware defined as anything that breaks the security model without the users knowledge.
Once installed malware will probe for emulator or physical device (won’t trigger if emulator is detected as an end user would not be running an emulator), what type of network connection: wifi,3G etc.
Malware actions i.e. what are they trying to achieve: to make use of premium services that the user is charged for (not until their next bill) or advertising i.e. the client is used as an SMS bot sending texts to a wider user community.
One infection discussed was simply installing a valid application (no Trojan), but the app contains a vulnerability that is exploited only when the victim connects to attackers website.
The majority of malware today is found on 3rd party stores, although some is also found on the Google store.
Summary: Apps can do almost anything; the speaker suggests the fix is not restricting this functionality but in comprehensively reviewing applications’ behaviour and ensuring they conform to their specified security model.
Geolocation of GSM devices – David Perez and Jose Pico
This talk focused on the Geolocaton of GSM (I.e. 2G devices) when there is no access to the phone network. The only thing known about the handset was the IMEI (i.e. the unique device) and IMSI (i.e the unique SIM) and rough location of the device. The scope was to produce a car based/portable solution.
The equipment utilised by the team was a portable fake GSM Base station (USRP1), Omni-directional and directional antennas (to pinpoint the exact location), Software the team used was in the form of Open Base Transceiver Station (OpenBST). All of the equipment needed to provide GPS data, triangulation and a user console.
Initially the team focused on distance estimation based on power measurements, this method failed and was soon discarded.
Time based triangulation could only locate devices plus or minus 500 meters, this was initially deemed to be a fail as it was not accurate enough (the inaccuracy was due to a delay introduced that was dependant on phone make/model/vendor).
This testing is illegal in most countries, however the team stated all testing was conducted in a country where it was legal….
The team did find a solution to the device introduced delays, but whilst results were much better after this problem had been solved, results were still not good enough.
The next issue was that when the team were impersonating the real network, no devices would register with the fake cell (phones didn’t see it), if tests were repeated with commercial BTS they did register why?
Power related issue? No
Beacons wrong? No, they were different between the fake and real cells initially but even after this had been fixed the issue still existed.
No precision of the clock (needs to be very precise) turned out frequency was too high by 900hz (the standard only allows for 45hz deviation) Fixed? Not entirely, devices did finally register to the fake cell but it still wasn’t working properly > the team bought a better clock > this finally solved the issue!
Once registered to the fake cell phones stayed registered for 1.8Km; within the range of the phone. Max distance device registered 15 meters, not enough power….could not beat the power of the real base station. You win this race by manipulating Cell Re-selection Offset (CRO); which is used for roaming between cells.
The final solution involved getting close to target and switching to directional antenna.
Here it was thought that the more power you receive from the target, you are pointing at target? This assumption was wrong, power fluctuated even when antenna was stable; the cause was BTS telling the target device to lower or raise it’s power….this was happening!
Fix = Disabled this mechanism in the OpenBST source code but only once the kit was close enough to move into directional mode…then the team finally had a WIN : )
With this final solution the team were able to pinpoint devices down to 20 metres (in an open field environment), these figures were not quite as good in an urban environment.
With this problem finally solved (after several months of work), the team stated their future work would be to attempt a solution for achieving the same for 3G networks. Whilst the team are limited by the fact that no open source 3G base station implementation exists they are optimistic that it is possible with 3G.