SSLurry – A quick and dirty .nessus file parser to extract hosts/services affected by SSL related issues.
I’ve been testing on a large number of heavily populated internal subnets recently. Accurately reporting SSL protocol/cipher and certificate related issues can be time consuming in such scenarios, time that can be utilised more effectively identifying issues not reported by automated scanners and/or assessing more significant issues.
Due to the sheer size of some target environments our testing remit may only extend to identifying services affected by common SSL related failings rather than detailing the more granular issue e.g. report the services affected by expired certificates but don’t detail the valid before/after dates.
To save some time and sanity in dealing with this problem the python3 script sslslurry.py was born.
sslurry usage:
sslurry truncated output:
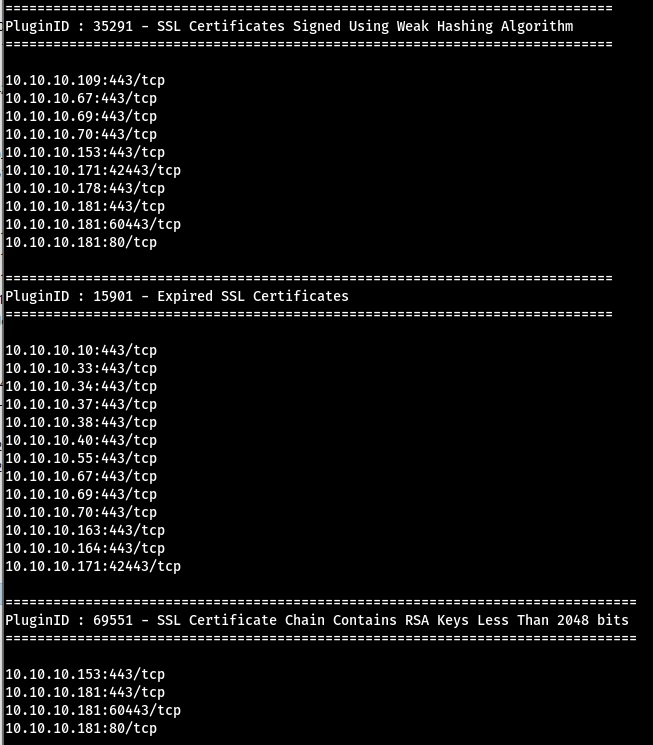
Obviously making use of sslurry should be caveated by the fact that the usual potential false positives reported by Nessus may still be present e.g. certificates being reported as untrusted even when signed by a trusted internal certificate authority.
sslurry can be found on github:
