Sorry but…..I’ve been seeing a lot of Covid-19 / Pandemic related words being used as passwords on internal tests recently. As a result the wordlist that should never have been needed…is here! covid2021-final.txt 173 MB file (50 MB .zip) The Torrent wasnt working too well, so migrated to here: https://github.com/attackdebris/wordlists sha1: 33b78622298a2cf2f59363a61cf6f6a4cb887e8a
Category: Tools
Nov 19
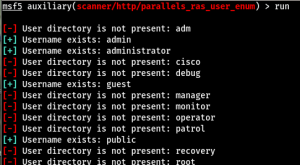
Parallels RAS Username Enumeration Flaw (CVE-2017-9447 Strikes Again?)
Earlier in the year I was assessing a network that contained a Parallels Remote Application Server (RAS). Parallels RAS is a remote working solution that provides access to virtual desktops and applications. It can run on both Windows and Linux and is typically seen on the standard HTTPS port. The platform has previously been affected …
Nov 16
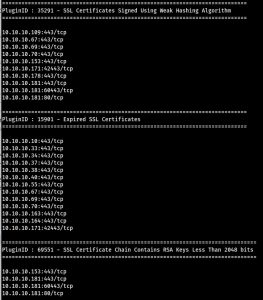
SSLurry – A Nessus SSL Issues Parser
SSLurry – A quick and dirty .nessus file parser to extract hosts/services affected by SSL related issues. I’ve been testing on a large number of heavily populated internal subnets recently. Accurately reporting SSL protocol/cipher and certificate related issues can be time consuming in such scenarios, time that can be utilised more effectively identifying issues not …
Feb 03
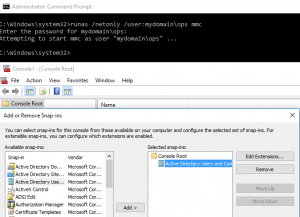
Low Privilege Active Directory Enumeration from a non-Domain Joined Host
Scenario You have recovered Domain User credentials for a domain but have no privileged or interactive access to any targets i.e. no Domain Admin account or any account that is capable of establishing an RDP session. Introduction On a recent engagement I was performing an internal assessment against several untrusted Windows domains. Using Kerberos Domain …
Jun 23
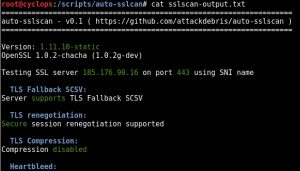
Auto-sslscan (Automatic SSL Scanning)
Auto-sslscan As I mentioned in the previous post whilst Nessus and Nmap do a reasonable job of enumerating SSL protocols and ciphers I often find myself utilising other 3rd party SSL scanning tools. One I find myself turning to on a regular basis is sslscan, I like the output it provides and issues become immediately …
Jun 23
Nmap-ssl-parser
Nmap-ssl-parser Nessus and Nmap both do a decent job of enumerating supported SSL protocols and ciphers from remote servers. However, I usually find myself also utilising other 3rd party SSL scanning tools. To that end I wanted an easy way to quickly parse out SSL services to an output file for input into other tools. …
Nov 09
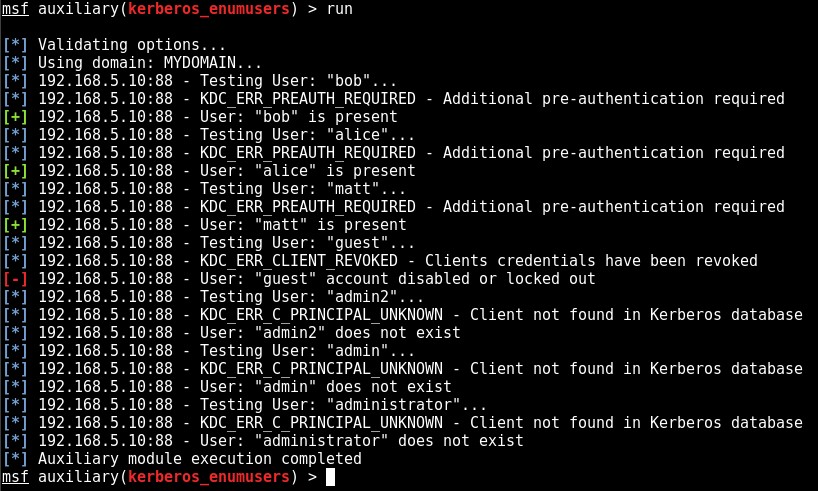
Kerberos Domain Username Enumeration
Kerberos Domain Username Enumeration Over recent years enumerating valid operating system level user names from up-to-date and well-maintained Windows environments, even from an internal test perspective, has become increasingly unlikely. Where RID cycling once provided us with a full list of domain users from an unauthenticated perspective, this is generally no longer the case. However, …
Oct 14
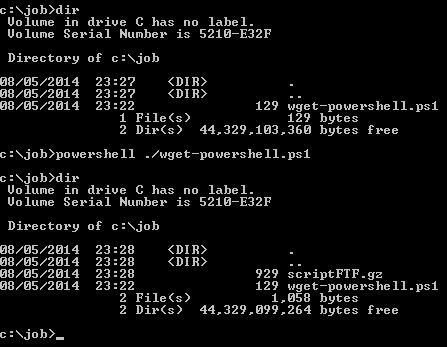
Babel Scripting Framework (babel-sf)
The Babel Scripting Framework (babel-sf) is a collection of custom scripts to facilitate useful pentest related functions via scripting languages. All of the following tools are replicated in the following languages – PowerShell, Perl, Ruby and Python: Portscanner ARPscanner FTP Client WGET Client Bind Metasploit Payload Reverse Metasploit Payload Why a custom scripting framework? babel-sf …
Feb 11
rundll32 lockdown testing goodness
I was recently on a Windows 7 workstation lock-down test which had been implemented pretty effectively with the vast majority of file and folder, service and AppLocker applied rules and permissions preventing the majority of malicious actions. However, I found that I was able to utilise rundll32.exe to attempt to enumerate/manipulate the environment. I couldn’t …
Aug 15
Old Incognito binary not working? or being eaten by AV? Then make your own
The original incarnation of Incognito has been around for a while it’s now a little dated and also picked up by the vast majority of Anti-Virus vendors. With this in mind I was intrigued by post by Josh Stone who has done a nice write up on creating an Incognito binary via the Metasploit Framework …
- 1
- 2