Earlier in the year I was assessing a network that contained a Parallels Remote Application Server (RAS). Parallels RAS is a remote working solution that provides access to virtual desktops and applications. It can run on both Windows and Linux and is typically seen on the standard HTTPS port.
The platform has previously been affected vulnerable by a directory traversal flaw. The issue allowing remote, unauthenticated attackers to exploit the flaw to read arbitrary files from vulnerable systems (CVE-2017-9447).
In this scenario testing revealed that the RAS service was no longer vulnerable to the directory traversal flaw, the issue having been mitigated in RAS version 15.5 Update 4, released in September 2017.
However, an issue that appears to be related to the fix for this previous flaw was identified. Whilst it was no longer possible to retrieve/read files via the directory traversal flaw. It was found to be possible to determine if a file or folder was present on the remote RAS server by leveraging the same payload. This could be achieved via the different server responses received:
A HTTP 403 (Forbidden) response being received when a folder/file is present
A HTTP 404 (Not Found) response received when a files does not exist
In relation to a Windows installation it is possible to leverage this issue from an unauthenticated perspective to enumerate valid local Windows usernames, assuming they have a home directory on the target system. Once account names have been enumerated, they can obviously be subjected to password guessing attacks.
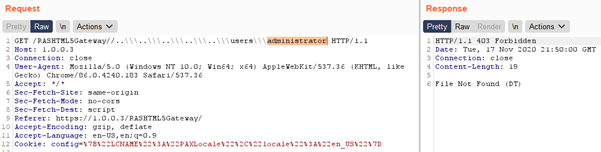
The following request is used to enumerate the “administrator” user. A HTTP “403 Forbidden” response from the server confirms the directory/user is present:
On the flip side the following HTTP request returns a HTTP “404 Not Found” which reveals the queried directory/user does not exist:
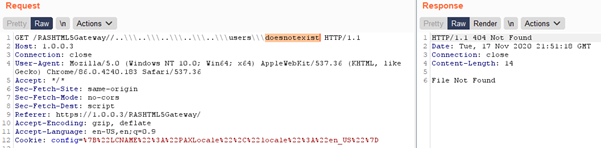
As a result of the above HTTP response discrepancies it is obviously possible to fuzz the username field to quickly enumerate any Windows users that may be present on the system.
Versions affected:
The original file directory traversal flaw CVE-2017-9447 was fixed in RAS version 15.5 Update 4, released in September 2017.
The file presence/username enumeration flaw discussed here, was fixed in RAS Version 17.1.2 released in July 2020. Ultimately as a result of a non-optimal fix this issue has been present for nearly 3-years.
Despite being in communication with the vendor, unhelpfully they opted to report the fix for this new 2020 flaw under the original 2017 CVE, which ultimately relates to an issue with a different impact.
Parallels Remote Application Server version 17 Release Notes
Release Notes snip below:
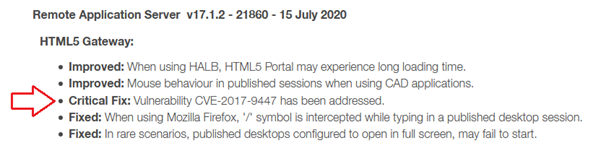
Timeline:
2nd June 2020 – Parallels Informed about the issue
15th July 2020 – Parallels released a patch
19th November 2020 – File presence/Username enumeration flaw publicly disclosed
I have created the following metasploit module to leverage this flaw, which will be pushed to the metasploit project in the coming days.
Here is the module in progress:
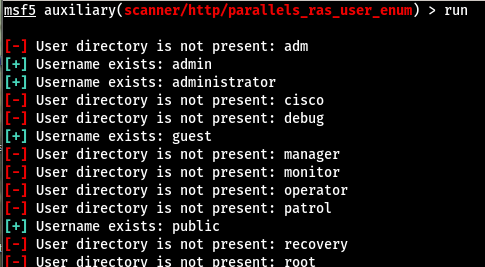
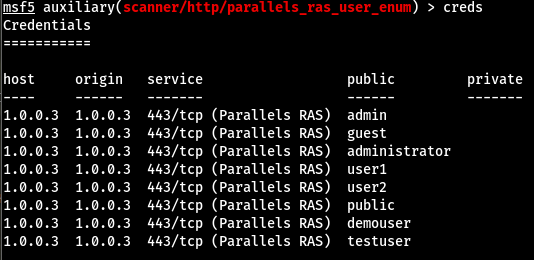
Here are the final results from the current wordlist:
The msf module can be downloaded from the link below:
