I haven’t seen too much detail around about how to crack Cisco ASA PBKDF2 (Password-Based Key Derivation Function 2) SHA-512 hashes, which I believe have been supported in some ASA versions from as early as March 2016.
As always the hashes can be recovered from the appropriate Cisco ASA config file.
Here are some examples of how the hashes can appear in the ASA config files. In the examples below all 3 sample hashes can be easily cracked using any respectable word-list:
enable password $sha512$5000$vlCP+V07DGEJ9TcSV/GpuA==$2S8SLoECmbtb/o17ZhXuKg== pbkdf2 username admin password $sha512$5000$SvZkzlRDO115YrLXsZuWCg==$Yu0w7sFjhLnbtZQJ/nyp+A== pbkdf2 privilege 15 username admin password $sha512$5000$OZ45Ro7002bnyFGXlIghqg==$T9oP1zKSTmv74Nizd8ku3A== pbkdf2 privilege 15
Some modification of the hashes is required before they can be imported into hashcat. Basically the first $ needs to be removed and all subsequent $’s need to be replaced with colons.
For example:
$sha512$5000$SvZkzlRDO115YrLXsZuWCg==$Yu0w7sFjhLnbtZQJ/nyp+A==
Becomes:
sha512:5000:SvZkzlRDO115YrLXsZuWCg==:Yu0w7sFjhLnbtZQJ/nyp+A==
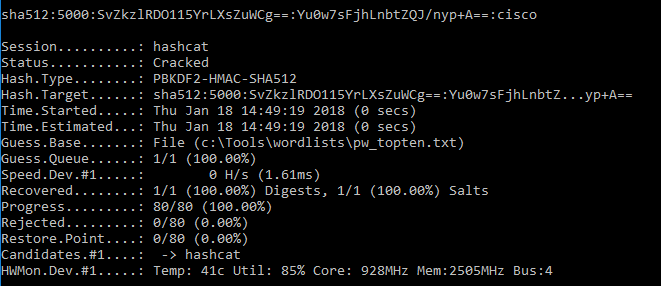
This hash can now be fed into hashcat as a single:
hashcat64.exe -m 12100 sha512:5000:SvZkzlRDO115YrLXsZuWCg==:Yu0w7sFjhLnbtZQJ/nyp+A== c:\Tools\wordlists\pw_topten.txt
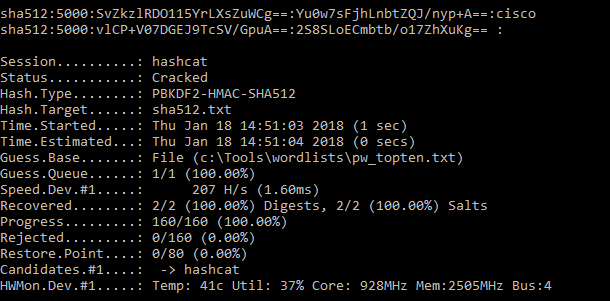
Or via a file:
hashcat64.exe -m 12100 sha512.txt c:\Tools\wordlists\pw_topten.txt
Cracked hashes:
sha512:5000:vlCP+V07DGEJ9TcSV/GpuA==:2S8SLoECmbtb/o17ZhXuKg==: (i.e. blank) sha512:5000:SvZkzlRDO115YrLXsZuWCg==:Yu0w7sFjhLnbtZQJ/nyp+A==:cisco
I leave the final hash (below) to be cracked as a challenge for the reader (it can be cracked with any respectable word-list):
$sha512$5000$OZ45Ro7002bnyFGXlIghqg==$T9oP1zKSTmv74Nizd8ku3A==
Thanks to my colleague Marius for the initial pointer on the hash type.